Imagine someone locking you out of your own house, digging through your sensitive documents, and thr...

Lorem ipsum dolor sit amet, consectetur adipiscing elit.

Imagine someone locking you out of your own house, digging through your sensitive documents, and thr...
As a featured guest on the The CISO Insights podcast Jacob Friedman told of his first unpleasant exp...

When a client asked about the difference between secrets management and password vaulting, I realize...

A free tool has been released by the Cybersecurity & Infrastructure Security Agency (CISA) called “U...

We now know the downside of AI in call center operations. As ChatGPT changes the nature of work, AI ...
What is a Group Policy? It’s the method by which many IT execs update and apply security and configu...
What is a decryption key? How is it used? And most importantly, what’s involved when it comes time t...
Cybersecurity insurance policies have been seen by CISOs as a last-resort safety net, but by 2023 th...
Technology leaders, CISOs have changed how they make purchasing decisions. Value Added Resellers (VA...
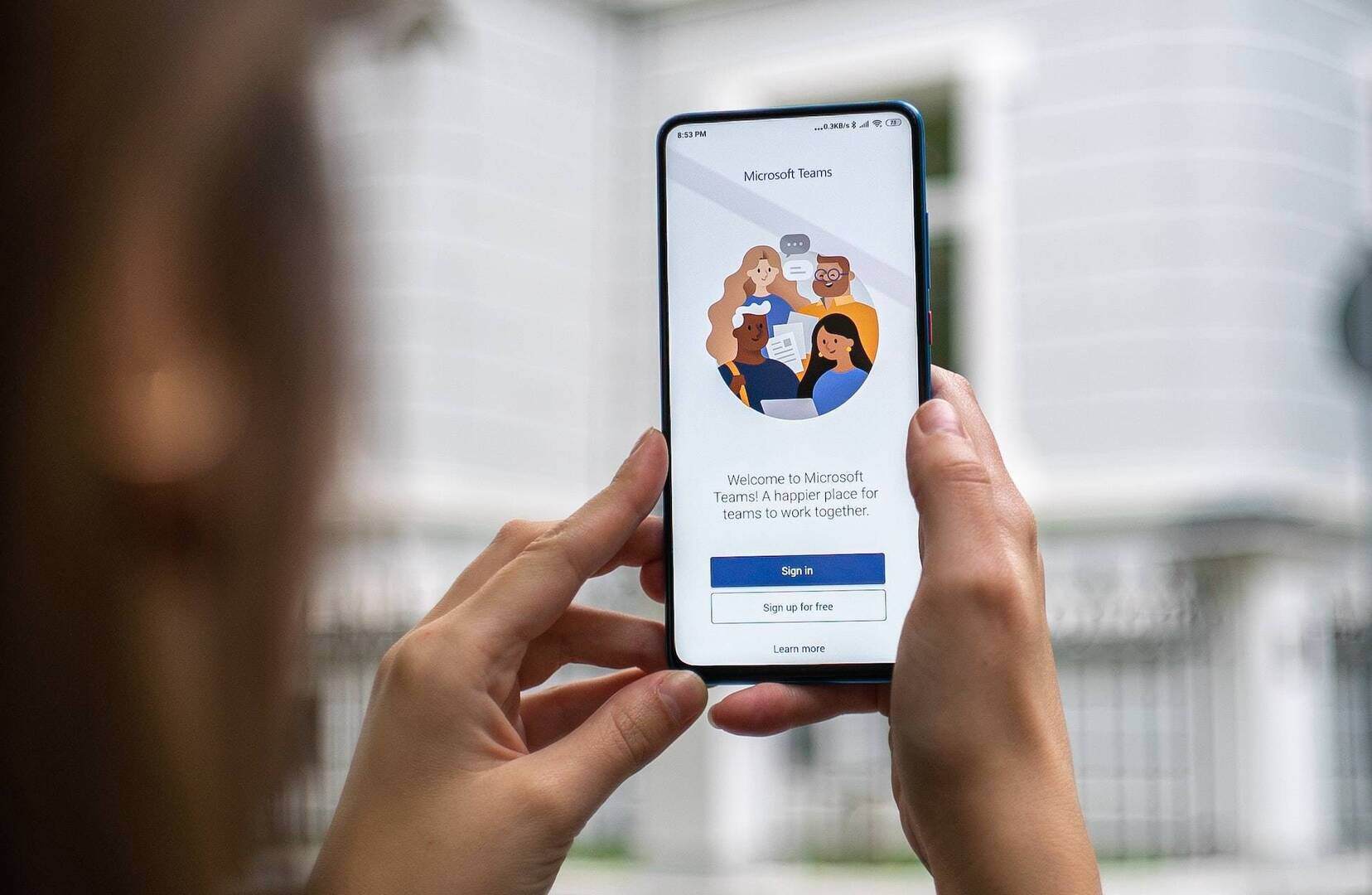
Why are Teams invites added to Zoom meetings? What, you thought it was just you? It’s actually commo...
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.